Cryptolocker continues to spread havoc on unprepared and unprotected computer systems throughout the world. Thousands of business and residential users are either losing their data or paying a ransom to retrieve their files. To update where we are some five weeks from our last report, the virus continues to evolve. While the evolution of viral infections is not unheard of, the mutations usually come in the form of copy cats, the copy cats change the file slightly to avoid detection and often change the user interface along with creating different ransom destinations. What differs with Cryptolocker is the fact that the virus infection is treated as a business. The secret to the scam succeeding is that they have to actually provide the decryption service or no one would ever pay. Without the decryption the business plan falls apart. This is a much more sophisticated attack that is making them millions.
The evolution comes in maximizing the chance that the victims will pay up. Here are things that can sabotage their scheme and how they deal with them.
If your computer is infected and your data files encrypted here is how things go. After encryption you are presented with a desktop wallpaper that looks similar to this.
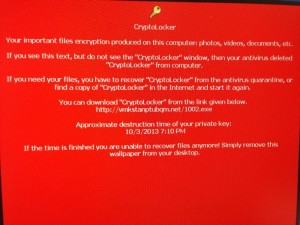
- cryptolocker wallpaper
Things that can go wrong at this stage are:
- Your antivirus program can remove the virus. While this sounds good, in this situation it is just the opposite. Your files are still encrypted and your pathway to be able to pay the ransom has been deleted.
- You try and do a system restore or otherwise alter the system state of the computer to remove the virus. This has the same result as number one.
- The program states you have 72 hours to pay by either Bitcoins or Western Union Moneypack. Both of these forms allow the recipient to remain anonymous. If the 72 hours has passed and you do not make payment they claim that the key needed to decrypted your files will be deleted.
As the developers saw potential “loss in sales” do to these variables they added some additional features to their extortion program.
There is a link on the desktop wallpaper to make payment as well as to download a new copy of the virus should you find yourself encrypted but uninfected do to scenarios 1. or 2.
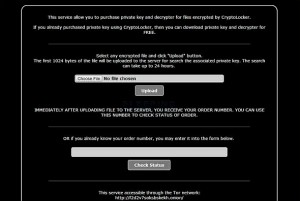
While it is a contradiction to their stated policy of deleting the key after 72 hours. they have graciously provided a new “service” whereby you upload on of your encrypted files and the system will scour their database to find the missing key to allow you to decrypt your files. Naturally for providing such a level of customer service their will be an increase in the ransom from $300 to $2000. Ouch!

In the last five weeks their have been some developments in how we try to prevent disaster from striking.
The first course of action is a cold back up, identify the key data files that need to be saved and back them up to an external source that can be detached from the system.
Next make sure that all your systems are thoroughly patched and updated, now more than ever is a great time to move away from Windows XP systems which will reach end of life next year, to a Windows 7 or 8 system which offers much greater security.
Education! Everyone in your home or company needs to be keenly aware of potential scams, bogus emails, unsafe surfing habits and what to look for to stop an infection before it can open a door for crypto locker.
Malware protection, make sure you have adequate protection against virus and spyware. Free programs at this point are not cutting it. Not only must you have active antivirus but the definitions need to be updated and the protection modules need to be enabled.
Traditional virus programs as of this writing are hit or miss. The nature of crypto locker is to dupe you into installing it. In this scenario it by passes many of the current security programs.
Computer Doctor of Hampden has helped support the development of a specific software program that closes a big hole and has the potential to stop cryptolocker and many other malicious programs in their tracks. What makes this software different is that it prevents the malware from being able to install itself. We own the rights to brand and distribute the software and have kept the price point very low to give you a fighting chance should this malware strike you, your family or your business.
Crypto Inoculator creates over 200 group policy rules that block crypto locker from installing. The system requires installation and configuration by one of our technicians, this allows software that is desirable to continue to work, and to ensure that there are no active infections currently on your system. After the virus check, the process of whitelisting takes a few minutes and the whole procedure can be done via remote connection to our office in Hampden. The software runs daily updates and can be configured to send you or one of our technicians an email if the crypto inoculator blocks a file. This notification will give us insight into what has caused the security breech and how to avoid it in the future. Computer Doctor of Hampden offers unparalleled, secure, remote service done locally.
creates over 200 group policy rules that block crypto locker from installing. The system requires installation and configuration by one of our technicians, this allows software that is desirable to continue to work, and to ensure that there are no active infections currently on your system. After the virus check, the process of whitelisting takes a few minutes and the whole procedure can be done via remote connection to our office in Hampden. The software runs daily updates and can be configured to send you or one of our technicians an email if the crypto inoculator blocks a file. This notification will give us insight into what has caused the security breech and how to avoid it in the future. Computer Doctor of Hampden offers unparalleled, secure, remote service done locally.

 creates over 200 group policy rules that block crypto locker from installing. The system requires installation and configuration by one of our technicians, this allows software that is desirable to continue to work, and to ensure that there are no active infections currently on your system. After the virus check, the process of whitelisting takes a few minutes and the whole procedure can be done via remote connection to our office in Hampden. The software runs daily updates and can be configured to send you or one of our technicians an email if the crypto inoculator blocks a file. This notification will give us insight into what has caused the security breech and how to avoid it in the future. Computer Doctor of Hampden offers unparalleled, secure, remote service done locally.
creates over 200 group policy rules that block crypto locker from installing. The system requires installation and configuration by one of our technicians, this allows software that is desirable to continue to work, and to ensure that there are no active infections currently on your system. After the virus check, the process of whitelisting takes a few minutes and the whole procedure can be done via remote connection to our office in Hampden. The software runs daily updates and can be configured to send you or one of our technicians an email if the crypto inoculator blocks a file. This notification will give us insight into what has caused the security breech and how to avoid it in the future. Computer Doctor of Hampden offers unparalleled, secure, remote service done locally.